Paid Partnership with Resolution
I remember a story from back in 2010 that is relevant to today’s post. Apple took the move to remove a popular iPhone camera App from the Marketplace. It all hinged on a “hidden” feature that allowed iPhone users to use the volume buttons as a shutter key to take pictures. Honestly, that was one of the best features of the App. Them removing an App is no controversy, but to do so only to release that very same feature in their next release…well, it looked shady at the time.
Atlassian is no Apple, and thank god. While more recently, they’ve preferred to acquire App Companies rather than try to supplant them by making features native, this wasn’t always the case. Today, we’ll look at an App that gave us a much-needed feature, only to have Atlassian later add similar functionality to Jira Data Center. However, SAML SSO for Jira by Resolution is still holding its own – and honestly is still my preferred solution when setting up Single Sign-On for Jira.
So, this review is going to be a bit different. I could spend all day talking about ALLLLLL the features that SAML SSO has – but no one has time for that. So rather than go over the complete list of features for Resolution’s solution, I think it’d be more interesting to look at what features their App provides that the built-in functionality cannot do – and even that is a relatively long list. So, without any more delay, let’s dig into this.
History Lesson
I first came across SAML SSO for Jira around 2016. Our company had just released its SAML Identity provider, and in that grand tradition known as dogfooding, they wanted all our services to use it for Single Sign-On. Which meant I had to figure out how to get it done in Jira and Confluence. Back then, there was no Data Center (and even the earliest version of DC lacked this feature), so we had to go with a Third-Party App.
This situation is where I first found Resolution. They were the only marketplace App offering the functionality – but they were all that was needed. Despite their rather thorough Documentation, My (relatively) newb self still needed some help, but Resolution was willing to help me along the way. Honestly, I was just confused about a few terms because our UI people decided to call it something different. But with their help, the deployment was a complete success. No joke, I had our sales engineers calling me asking how we did it, as they had customers who wanted to Integrate Jira, and they knew it was possible because we were doing it.
It was some time after I left this company that Atlassian came out with the SAML feature in Jira Data Center, but whenever I look at it, I can’t help but see some of the holes that Resolution Apps cover. So when it came time to do my omnibus review, of course, I included them. But, I’d still like to take a closer look and see why I still prefer them over the built-in offering and hopefully convinced a few of you that they are well worth the extra expense.
Features
User Directory Synchronization
So let me be clear here; most SAML consumers – including Atlassian’s – allow you to provision a user from the SAML Attributes. And that is enough to, generally speaking, get a user off the ground. But what then? Also, how do you address shortcomings in your Identity Provider (IdP)? Like the gem I discovered where Azure AD would only send groups for a user only if they are in less than 100 groups.
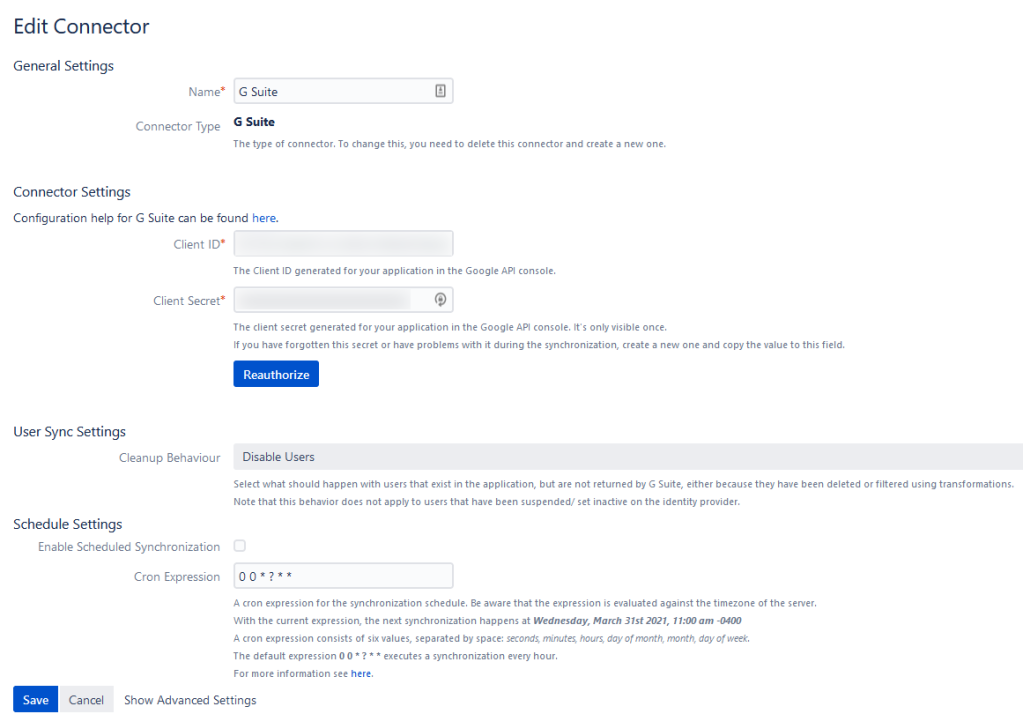
This problem is where Resolution shines through, though. Not only will it engage other APIs from Azure to collect this information – you can set it up to sync information automatically using UserSync. All the power of an LDAP sync, but in SAML+API form! How can you lose?
Multi IdP Selection
So I don’t know about your company, but for most large companies I’ve worked for, Authentication is fragmented at best. You have the core company that is still using one solution because it’s always worked for them. You have this other Business unit purchased in an acquisition some years ago that’s somehow still doing its own thing. Then you have the latest acquisition that was some small up-and-coming product that uses something you’ve never heard of. And your job, poor Jira Admin, is to get all of these people authenticated into Jira – and no one is willing to change their authentication method.
Well, this is another area where SAML SSO for Jira can help out. It actively supports multiple IdP so that you can set them all up simultaneously. It also gives you the ability to set the method by which it selects the appropriate IdP. In one method, it will then ask the user which IdP do they want to use, based on their situation – they click, authenticate, and they’re in! In another, it will “Automagically” select the correct IdP based on their email address.
Transformations of SAML Attributes
So this came up recently. I had a client whose IdP sent the primary identity as their users’ full email (for example, [email protected]). However, as this was a migration, we needed it to match their existing username scheme, which was the part before the “at” symbol. So – typically, we’d be stuck, right? Have to figure out some way to change everyone’s user id so they could log in but preserve their history?
Uh – no. With a bit of Regex knowledge, you can transform the field to give you what you need! [email protected] becomes rnissen.

Debugging tools
The worst thing that can happen for a Jira instance is your users can’t log in. If they can’t log in, it doesn’t matter how well run your instance is; it’s still useless to them. So having tools to debug these issues and get support quickly is Vital with a capital V.
Thankfully this is another point where SAML SSO shines through. I mean – you don’t have to go hunt in logs and hope it captured what you needed at this random time. No – it captures debug information for recent logins automatically and gives you a handy list.
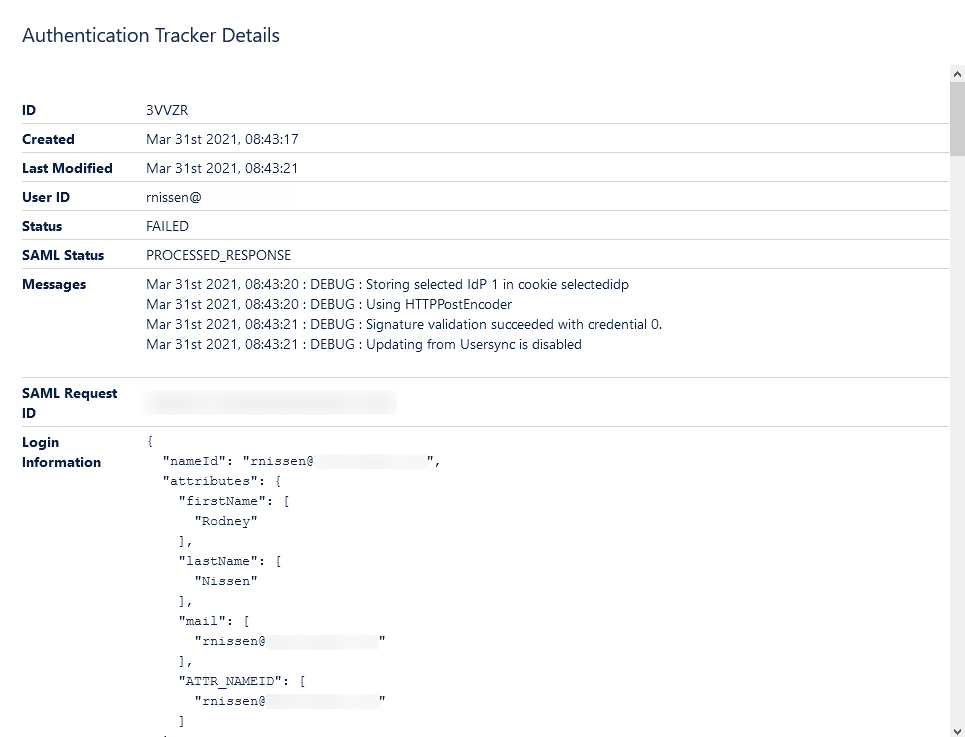

No – seriously, the information here will save your job. I’m just showing one example here – but looking here, it tells me what failed and why it failed. In this case – this test was done before I set up the afore-mentioned RegEx Transformation – and it couldn’t match my email to a username. Setting that up fixed it right up, and my next login was successful.
Exportable Configuration
Just saying – configuration portability is a problem in Jira. I know it, you know it, and I believe even Atlassian knows it. It is a pain in the butt to move configurations from one instance to the next. Why does this matter in a review about an App? I have a point here, I promise.
Ideally, you should test changes in either a Dev or Stage instance, then export those changes from that instance, import it into the next highest, and then finally up into Production. In Jira, though, you have to redo these changes by hand in each instance. That is a place where you could forget a step or introduce a mistake – meaning you have to redo testing on each stage of deployment. This situation – to use the common phrase – is no Bueno.

Thankfully, SAML SSO is one section of the configuration where that is not the case. You can export your whole IdP configuration, go up to the next instance, and redeploy it. It should be noted that it is not saved automatically after you import – and there is a reason for that. With SAML, you will need to change some URLs and certificates over to a different configuration before hitting save – so the App gives you a chance to do so. Just be sure to hit “Save” when you finish.
I know I mentioned Documentation and Support already, but…
Resolution is THOROUGH with their Documentation. You need Just-In-time Provisioning using GSuite along with UserSync and SSO? There’s a Doc for that. Configuring using Okta, OneLogin, AWS, or Salesforce instead? Check, Check, Check, and check. In fact: here’s the complete list:
- Microsoft AD FS
- Azure AD
- Gsuite
- OKTA
- OneLogin
- Auth0
- Gluu Server
- AWS
- Bitium
- Centrify
- DUO Access Gateway
- Keycloak
- OpenAM
- PingFederate
- PingOne
- RSA SecurID Access
- Salesforce
- WSO2
- JumpCloud
- Azure AD B2C
And yes, that’s not every IdP on the planet. For example, VMware’s Workspace One Access. There is no documentation for it with Resolution. But I know for a fact that their support can walk you through it. How do I know? Because: been there, done that.
Again, this is a product I’ve been using at various companies for years. From my experience, Resolution is a partner in your deployment. If you need help, they have experienced support and thorough Documentation to help you through any challenges you face.
My Analysis
What this App does well
I’ve stated before that I view the best Apps of the Atlassian marketplace in two broad categories. One of the “Swiss Army Knives” (those that do a bit of everything). Then you have Apps like SAML SSO. They only do one thing, but they do it very well. To be clear, this is not a criticism at all. Focusing on User Authentication and provisioning has allowed Resolution to hone this App to one of the best in the Marketplace – and one I consider a must-have in most cases.
What this App could work on
So, if this is your first time using the App – it can be overwhelming. Sometimes you will have mismatches in terminology to manage, and if you are inheriting an instance with this already set up, you are greeted by a wall of options. Granted – you can leave most of them to the defaults; they are still there. It is an intimidating App.
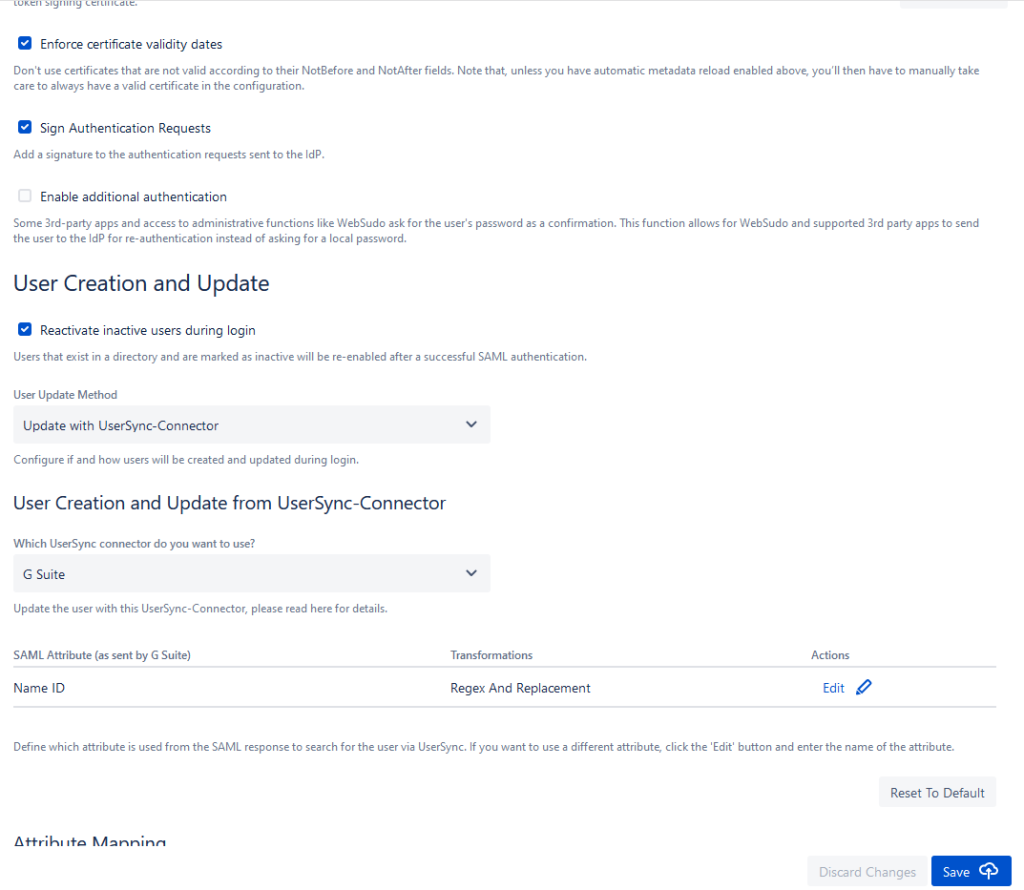
I do see movement on this. Believe it or not – the problem here used to be worse. I even see some sections that link to the appropriate Documentation – which helps immensely.
User Map’s Tier Rank

So, no surprise here, considering I already ranked it, but I’m keeping Jira SSO at an “A” Rank. You won’t need it for every Jira instance you’re on, but if you have a requirement to integrate with a SAML provider, I consider this App a “Must-have”.
So, about last week and next month.
Just saying, I HATE missing a post week. No – really – I’ve been in a funk over it all week. But, you cannot change the past, only learn from it. What did I learn? Well, for starters, maybe publishing day isn’t the day to be running experiments that can cripple your whole network.
That being said, we are back this week, and we’ve got a strong April planned. Here’s how things are lining up:
- April 14th: We’ve got another sponsored spot for Elements Connect. This is a new App for me, but I’ve been playing around with it – and can see it solving a few problems I’ve had over the years.

- Also, on April 14th: We’ll be speaking with AppFox, Deiser, and Atlassian. I am super excited to be given a chance to speak with you and answer your questions! I hope to see all of you there.

- April 28-30th: Team ’21 is kicking off! I’ve gotten a chance to see some of what Atlassian is working on, and even though it’s just a fraction of what I expect them to do, it’s going to be awesome. I’ll likely do two articles to cover each of the keynotes with all the juicy new features.

- Also, the Week of Team ’21: You really think one bonus post was enough for Team ’21? Heck, No! I’ll also be doing two additional posts to cover some new products and such coming out. I can’t say for whom and what just yet – I have a whole new “appreciate” for media blackout dates – but I cannot wait to share this with you.
To sum it up: I’m going to spend most of April writing articles. XD
So what do you think?
Have you used Jira SSO? Are you considering it now? Let me hear from you in the comments! Don’t forget you can follow us on the Social Media Platform of your choice. You can find us on Twitter, Facebook, Linked In, and Instagram, where we’ll have the latest from the blog, news from the Atlassian Community, and more! You can also get the latest blog posts delivered directly to you as soon as they publish. All you have to do is fill out the form at the bottom of the post. No, seriously, what are you waiting for?
But until next time, this is Rodney, asking, “Have you updated your Jira issue today?”

1 Comment